Use directory services with VERDE dynamic virtual desktops by configuring VERDE to connect to any LDAP-compliant directory. There are two connectors provided:
- Optimized connector for Active Directory. To join a virtual desktop to Active Directory, the host server must have DNS set to the address of the Domain Controller.
- LDAP connector that works with other directories such as OpenLDAP, Novell eDirectory, and IBM Tivoli DS. Once the LDAP connection is configured in the VERDE Management Console, session settings are used to assign settings.
The Session Settings function on the VERDE Management Console has the ability to enable Windows Guest sessions, but Linux guest sessions will require a third-party application to authenticate with a directory service. This is because Linux virtual desktops require configuring the virtual desktop itself to join a domain. Additionally, this method may not provide single sign-on (SSO), because users must authenticate to VERDE and then authenticate to their respective virtual desktops once VERDE authorizes them.
To add a new LDAP compliant directory, complete the following steps:
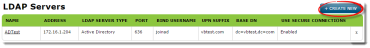
- Open the LDAP Servers screen.
- Select "CREATE NEW."
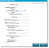
- A new window will appear. In the field beside "Name," enter a name for this connection. Names are case sensitive and cannot be changed once added. A directory user is represented in VERDE in the form of
<user>@<name>where<name>refers to the name listed here for this directory. This is the format that is used for VERDE Management Console login, Desktop Policy, and Session Settings.Directory groups are represented as
<group>@<name>. In Desktop Policy, the group is specified as%<group>@<name>. The name must be unique so that users are correctly identified. Note that the UPN Suffix can be repeated across multiple LDAP specifications VERDE. This enables creation of different connectors and Desktop Policies for different OUs within the same directory. - Use the "Validate LDAP Server" option (enabled by default) to confirm that the connection information is valid. Do not select this option if only a branch server is connected to the LDAP server.
- Select "LDAP" or "Active Directory."
- Enter the information listed in the LDAP Settings table to define a connection.
- Save the settings. You'll see the new LDAP server on the LDAP Servers screen. Users and groups can be assigned to the server through a Desktop Policy.
| Setting | Description |
|---|---|
| Address | The host name or IP address of the directory server. The VERDE cluster master uses this address to access the server. Multiple addresses can be entered, separated by comma. For example, 132.16.1.204, vbad.NComputing.com. When setting up the LDAP connection, VERDE will try to bind to all the addresses listed in order until an available server is found that authenticates the admin user and can read the groups for that user. |
| Port | The LDAP server listening port. The secure port is recommended. The default SSL port is 636. The non-secure port is 389. |
| Bind Username | The user belonging to this directory that has permissions to view the entire directory (or OU) as specified in the LDAP connector. For OpenLDAP, this username is represented as a distinguished name (DN), such as cn=administrator, dc=group, dc=company, dc=com. Confirm that the user has permission to do the following: Search the directory under the subtree specified by the Base DN to: look up specific user, look up specific group, look up groups for given user. Change account passwords. |
| Bind Password | The bind username account password. |
| Confirm Bind Password | Confirm the password. |
| Base DN | The base distinguished name (DN) which is a unique identifier used to limit the search space. For example, to limit the search to the technical sales group, enter OU=technical,DC=sales,DC=com. The search is limited to the technical OU (Group), rather than the whole directory tree. To locate these settings on a Windows Server (2003 and 2008), run the dsquery command, for example: $ dsquery user -name administrator "CN=administrator, CN=Users, DC=sales, DC=com." This lists a DN for administrator. A base DN can be constructed as DC=sales, DC=com. This is field is required for OpenLDAP. For eDirectory, the base DN is entered as o=company. An administrative DN may be cn=administrator, o=company |
| Use Secure Connections | If the port entered is an SSL port, select this check box. |
LDAP has additional settings on the Advanced Settings tab. Use the listed default settings, or edit the settings to your needs.
- Username Attribute. Specifies the LDAP attribute name that defines the username.
- Group Attribute. Specifies the LDAP attribute name that defines a group.
- Group Entry ID. Specifies the LDAP attribute on a group that identifies all members belonging to that group.
| Setting | Description |
|---|---|
| Address | The host name or IP address of the directory server. The VERDE cluster master uses this address to access the server. |
| Port | The LDAP server listening port. The secure port is recommended. The default SSL port 636. The non-secure port is 389. |
| Blind Username | The user belonging to this directory that has permissions to view the entire directory (or OU) as specified in the LDAP connector. For Active Directory, this is a name, such as administrator. Confirm the user has permission to do the following: search the directory under the subtree specified by the Base DN to: look up specific user, specific group, and groups for the given user. Change account passwords. |
| Blind Password | The bind distinguished name (DN) account password. |
| Confirm Blind Password | Confirm the password. |
| UPN Suffix | The User Principal Name (UPN) suffix, without the (@) symbol. For Active Directory, enter in format dictated by the directory structure, such as sales.com. |
| Base DN | The base distinguished name (DN) which is a unique identifier used to limit the search space. For example, to limit the search to the technical sales group, enter OU=technical,DC=sales,DC=com. The search is limited to the technical OU (Group), rather than the whole directory tree. To locate these settings on a Windows Server (2003 and 2008), run the dsquery command, for example: $ dsquery user -name administrator "CN=administrator,CN=Users,DC=sales,DC=com" This lists a DN for administrator. A base DN can be constructed as DC=sales, DC=com. This is field is optional for Active Directory. |
| NT4 Domain Name | Windows NT 4.0-style domains do not support DNS naming, and require a unique (for that network) NetBIOS name assigned for the domain. If the domain intends to support clients for Windows NT 4.0-style domains, enter a NetBIOS name. |
| Use Secure Connections | If the port entered is an SSL port, select this check box. |